Securing identities at every interaction
Delinea makes you more secure by centralizing authorization to govern those interactions seamlessly. Delinea is pioneering how organizations apply context and intelligence throughout the identity lifecycle across cloud and traditional infrastructure, data, and SaaS applications to eliminate identity-related threats.
Seamless, intelligent, centralized authorization to better secure the modern enterprise.
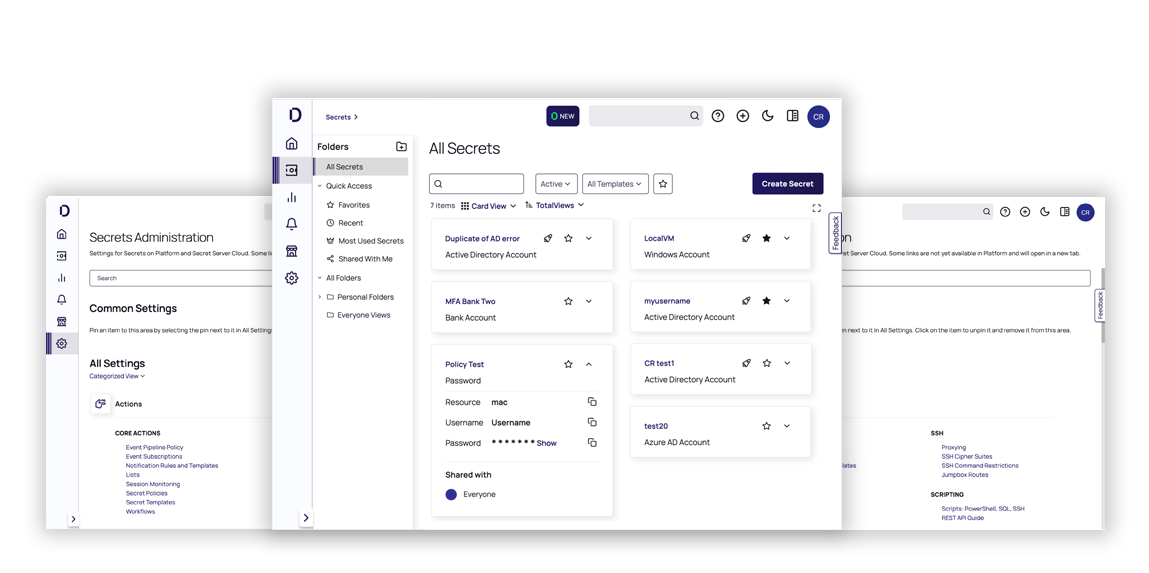
Secret Server
Protect your privileged accounts with our enterprise-grade Privileged Access Management (PAM) solution. Available both on-premise or on the cloud-native Delinea Platform
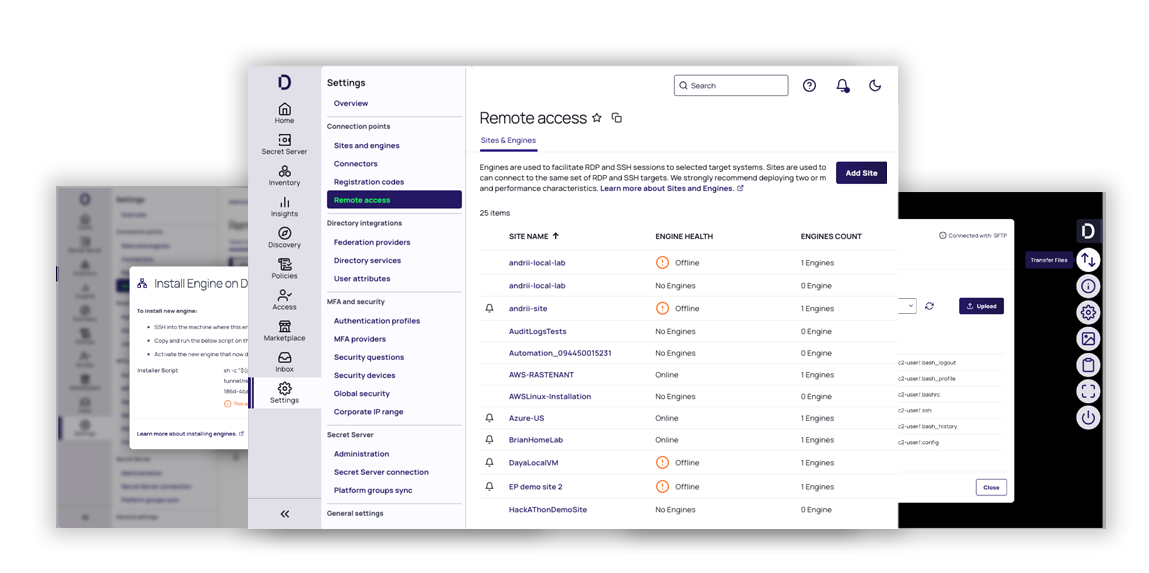
Privileged Remote Access
Remove risk, not remote users, with a browser-based, VPN-less approach to accessing critical internal resources
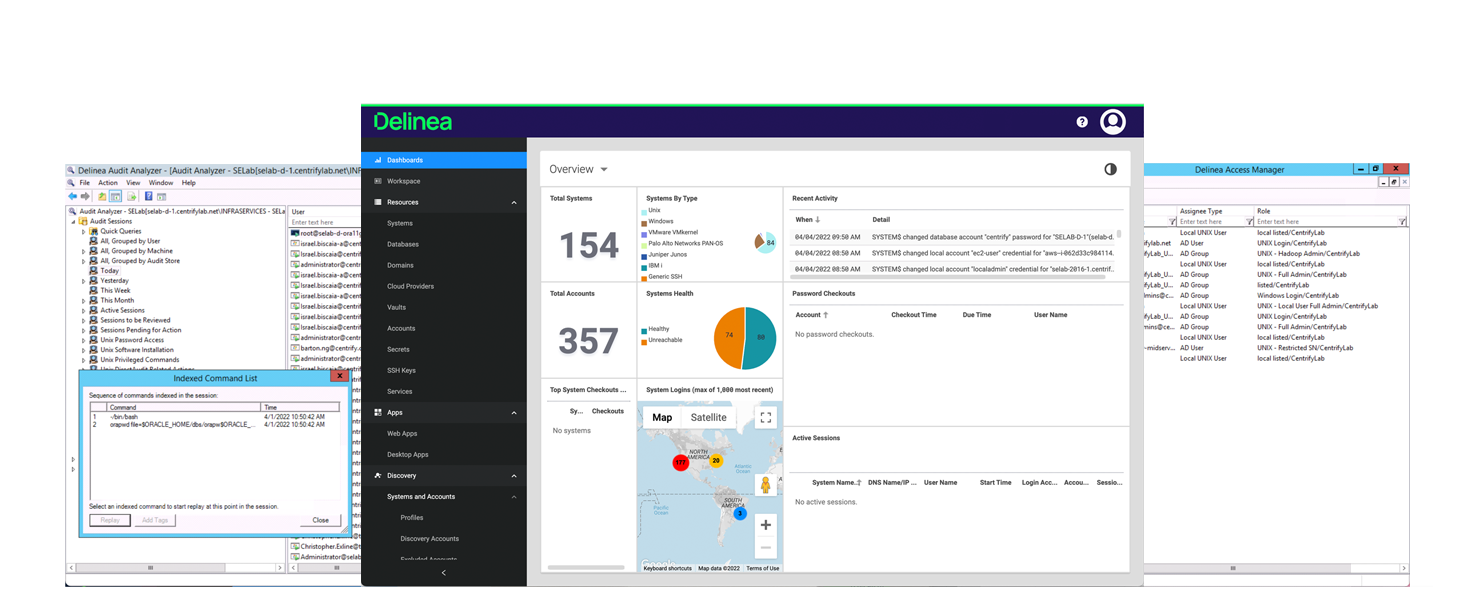
Server PAM
Protect privileged access to servers with identity consolidation and centralized management of just-in-time and just enough privileges across Windows, Linux, and Unix servers.
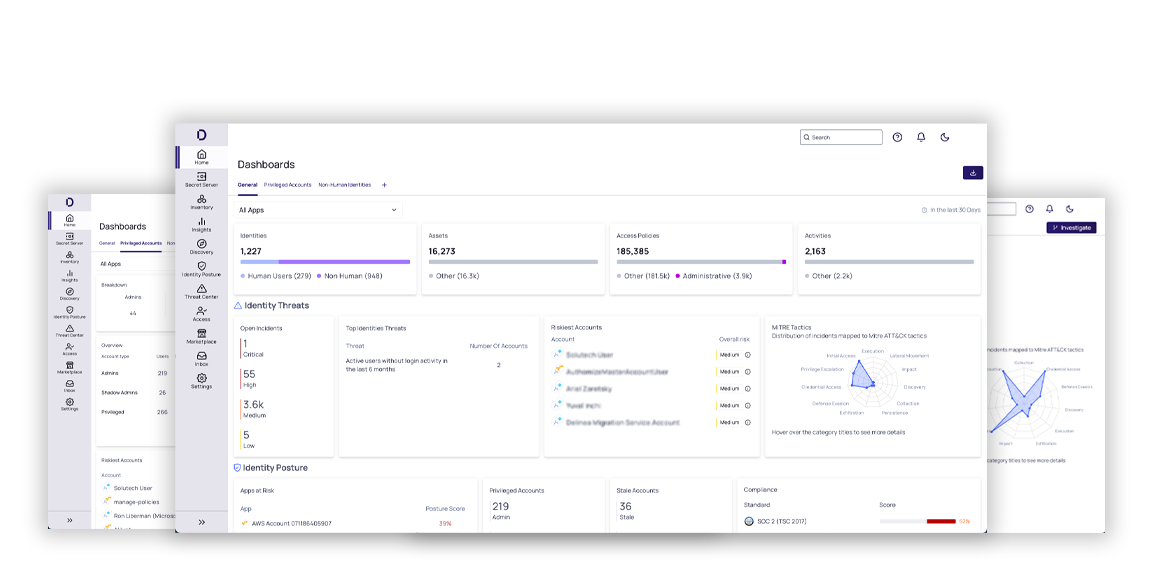
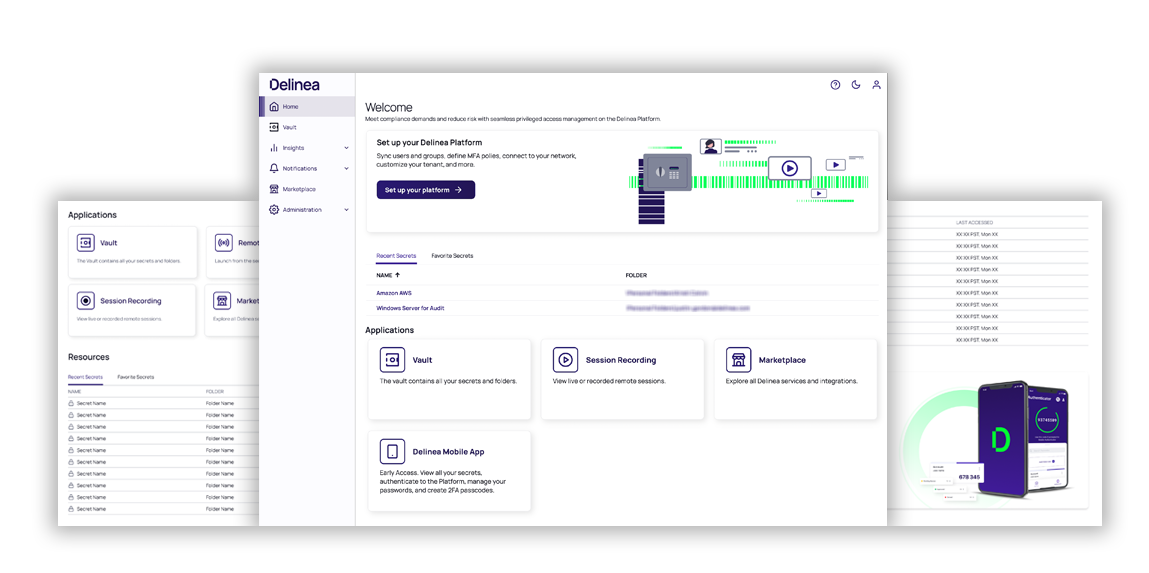
Delinea Platform
Seamlessly build and apply context across all identities with intelligent authorization
Competitive Advantage
THE BEST VALUE IN COMPLETE PRIVILEGED ACCESS SECURITY
Centrify Zero Trust Privilege combines password vaulting with brokering of identities, multi-factor authentication enforcement and “just enough” privilege, all while securing remote access and session monitoring of all privileged sessions.
- GRANT LEAST PRIVILEGE
- AUDIT EVERYTHING
- ADAPTIVE CONTROL
RECOGNISED MARKET LEADER BY ANALYSTS
- Leader in Privileged Identity Management (PIM) Forrester Waves Report
- Leader in Gartner Privileged Access Management (PAM) Magic Quadrant
- Lead amongst our peers review by Gartner Peer Insight, G2Crowd and TrustRadius
SECURE PRIVILEGED ACCESS WITH A RADICALLY DIFFERENT APPROACH
Grant least privilege access based on verifying who is requesting access, the context of the request, and the risk of the access environment.
- VERIFY WHO
- CONTEXTUAL REQUEST
- SECURE ADMIN ENVIRONMENT
Ensure Clean Source, Distributed Jump Posts, Secure Remote Access