Identify threats. Secure data. Reduce risk.
Stealthbits Technologies, Inc. is a customer-driven cybersecurity software company focused on protecting an organization’s sensitive data and the credentials attackers use to steal that data. By removing inappropriate data access, enforcing security policy, and detecting advanced threats, our highly innovative and infinitely flexible platform delivers real protection that reduces security risk, fulfills compliance requirements, and decreases operational expense.
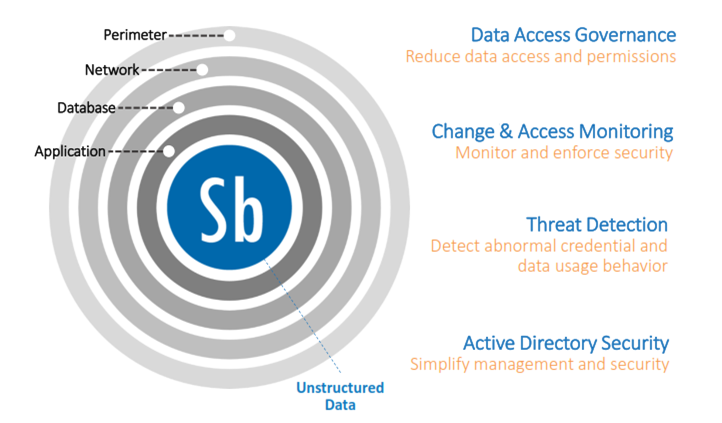
Stealthbits secures your credentials and data through Data Access Governance, Change & Access Monitoring, Threat Detection and Active Directory Security.
Explore STEALTHbits Solutions
With Stealthbits, There’s More to Data-Centric Security
Data Access Governance
Reduce data access and permissions to appropriate levels.
Active Directory Security
Manage and secure Active Directory – the mechanism that supplies access to all your data.
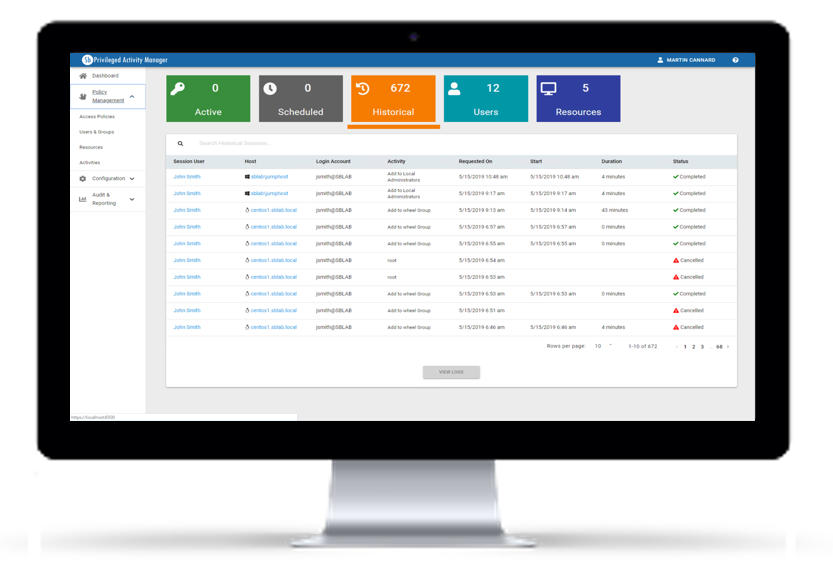
Privileged Access Management
Control privileged activities and delegate administrative access safely.
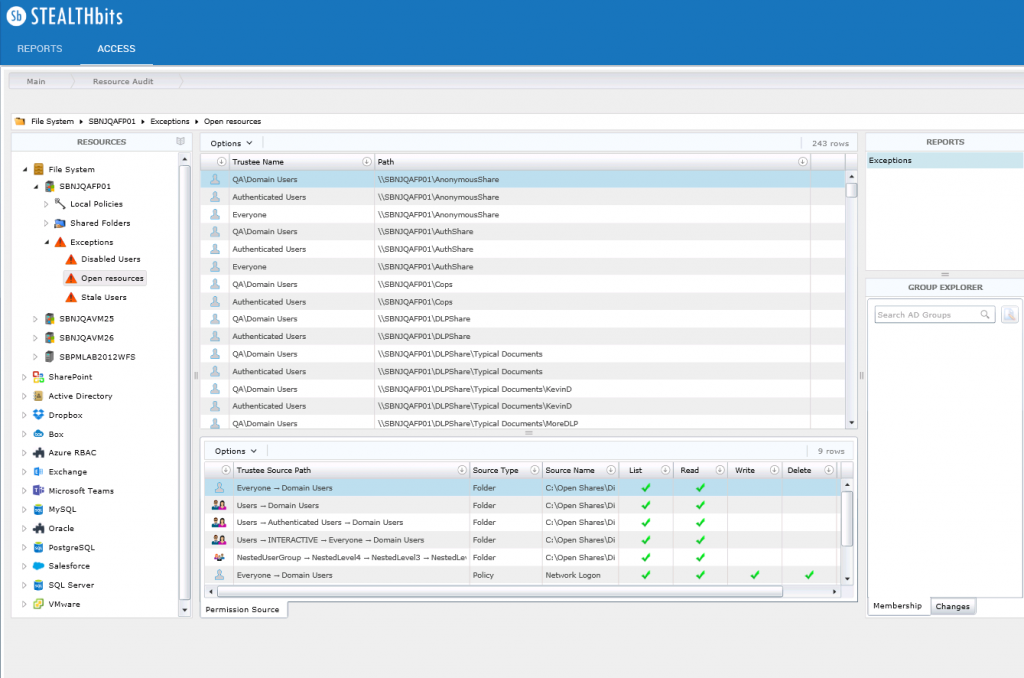
StealthAUDIT® Management Platform
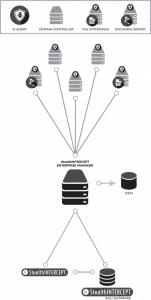
StealthAUDIT is a management platform designed to automate data collection, analysis, remediation, governance, and reporting tasks associated with the management and security of credentials and data. Its speed, lightweight footprint, and agent-less, open architecture enable organizations to discover and remediate security risks at scale, while simultaneously creating operational efficiencies through interoperability.
StealthINTERCEPT® ACTIVE DIRECTORY MONITORING
StealthINTERCEPT enables organizations to monitor the usage of credentials and data, as well as enforce security policy in real-time. Through visibility into every change and access activity across unstructured data repositories and critical applications, StealthINTERCEPT detects and analyzes suspicious behaviors, proactively prevents changes and access, alerts, and integrates directly with the market’s leading SIEM platforms, all without any reliance on native logging.
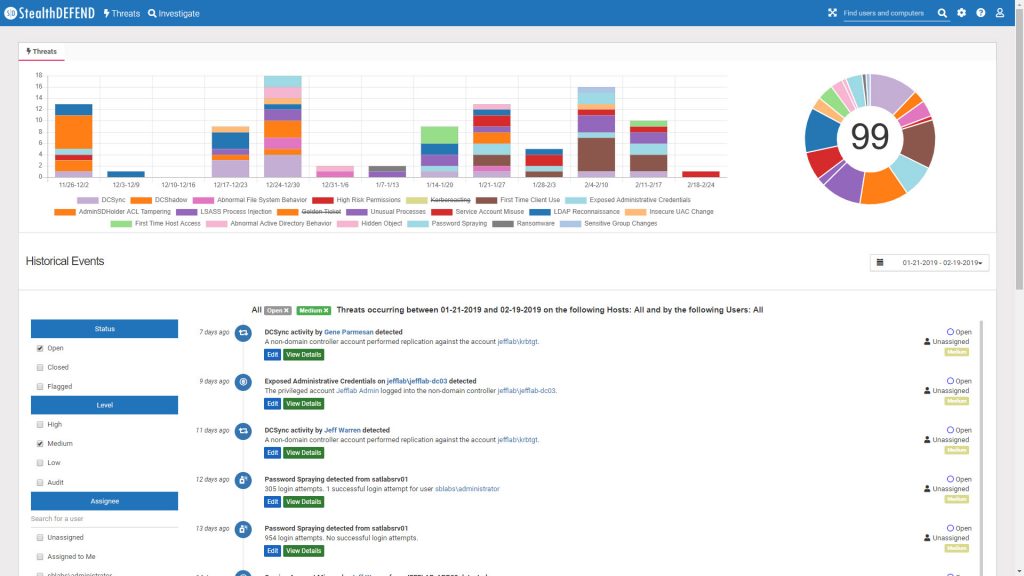
StealthDEFEND® Real-Time Threat Detection & Response
Every attacker is after the same two things; credentials and data. Once inside, attackers aim to discover your environment, find and compromise privileged credentials, and leverage those credentials to access, exfiltrate, or destroy data. StealthDEFEND is the only real-time threat detection and response solution purpose-built to protect these two common denominators in every breach scenario.