THINK ZERO TRUST PRIVILEGE. THINK CENTRIFY.
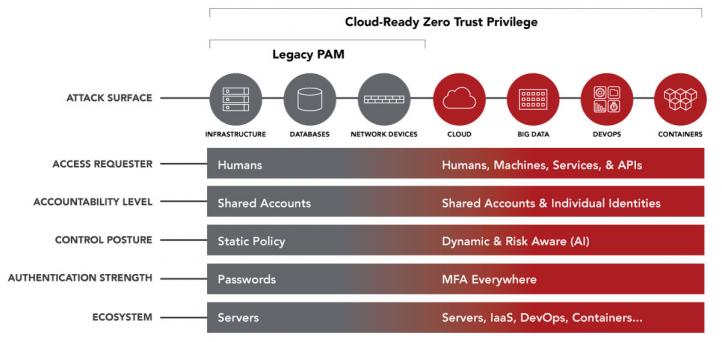
Centrify is redefining the legacy approach to Privileged Access Management (PAM) with cloud-ready Zero Trust Privilege to secure modern enterprises and stop the leading cause of breaches – privileged access abuse. Zero Trust Privilege services help customers grant least privilege access based on verifying who is requesting access, the context of the request, and the risk of the access environment. By implementing least privilege access, Centrify minimizes the attack surface, improves audit and compliance visibility, and reduces risk, complexity and costs for the modern, hybrid enterprise.
ZERO TRUST PRIVILEGE SERVICES
PUTTING CORE PRIVILEGED ACCESS CONTROLS IN PLACE
The Centrify Privileged Access Service allows customers to establish the core privileged access controls across your growing attack surface.
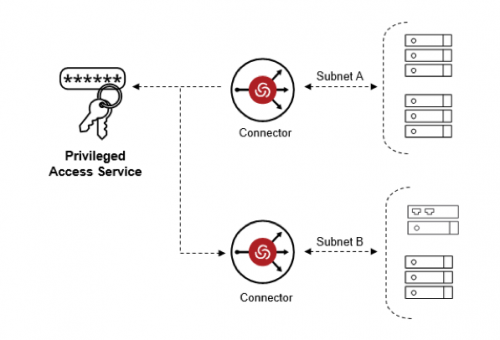
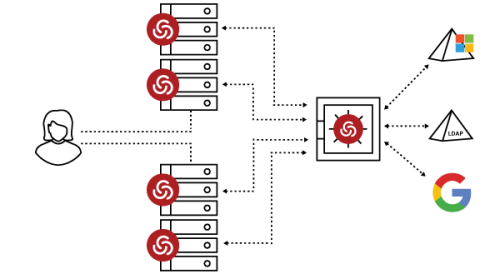
GOING BEYOND DISCOVERING & VAULTING PASSWORDS
The Centrify Authentication Service provides customers with the needed capabilities to go beyond the vault and reduce their attack surface by consolidating identities and eliminating local accounts as much as possible.
ESTABLISH LEAST PRIVILEGE ACCESS TO REDUCE ATTACK SURFACE
The Centrify Privilege Elevation Service empowers customers to implement privilege elevation controls as well as workflow for just-in-time privilege access.
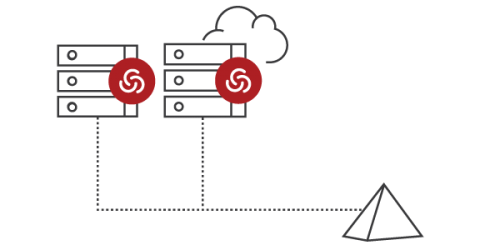

HARDEN YOUR ENVIRONMENT WITH HIGH ASSURANCE
The Centrify Audit and Monitoring Service allows customers to fulfill their compliance mandates through auditing and reporting as well as shut down any dangerous workarounds by putting host-based monitoring in place.
PINPOINT PRIVILEGED ACCESS ABUSE IN NEAR REAL TIME
The Centrify Privilege Threat Analytics Service leverages advanced behavioral analytics and adaptive multi-factor authentication to add an additional layer of security and allow for near real time alerts of abnormal user behavior.
Competitive Advantage
THE BEST VALUE IN COMPLETE PRIVILEGED ACCESS SECURITY
Centrify Zero Trust Privilege combines password vaulting with brokering of identities, multi-factor authentication enforcement and “just enough” privilege, all while securing remote access and session monitoring of all privileged sessions.
- GRANT LEAST PRIVILEGE
- AUDIT EVERYTHING
- ADAPTIVE CONTROL
RECOGNISED MARKET LEADER BY ANALYSTS
- Leader in Privileged Identity Management (PIM) in Q4 2018 Forrester Waves Report
- Leader in Gartner Privileged Access Management (PAM) Magic Quadrant in Q4 2018.
- Lead amongst our peers review by Gartner Peer Insight, G2Crowd and TrustRadius
SECURE PRIVILEGED ACCESS WITH A RADICALLY DIFFERENT APPROACH
Grant least privilege access based on verifying who is requesting access, the context of the request, and the risk of the access environment.
- VERIFY WHO
- CONTEXTUAL REQUEST
- SECURE ADMIN ENVIRONMENT
Ensure Clean Source, Distributed Jump Posts, Secure Remote Access